In the middle of a kitchen refit, our central heating (CH) system started experiencing frequent drops in pressure that required refilling for re-pressuring the boiler. Such drops in pressure can be for several reasons, some trivial and some serious and it is important to find the root cause (more on this later). Investigation for the
Category: Conceptual Modelling
Language Support for Multi Agent Reinforcement Learning: Our paper at ISEC 2020
Our research with TCS Research Labs continues to bear fruit. The Actor based language ESL used for much of our collaborative research now incorporates machine learning capability and delves into Digital Twin technology. We report on some early results at one of our favourite conferences: Innovations in Software Engineering (ISEC) – India’s premier software engineering
The Link between Vienna, Fake Art, John Le Carre and Anthony Blunt
One of the great joys of travelling to different locations is to try and establish obscure links between things that you see on location and what you already know. So what connects the semantics of forged art with spies and Vienna? To establish the relationship you have to go Europe’s only art gallery devoted to
Are we all ‘Digital subalterns’ now?
In 1988, the postcolonial theorist, Gayatri Spivak published an essay “Can the Subaltern Speak?” about the appropriation of Gramsci’s “subaltern” (the economically dispossesed) term. She was critical of the effort to collect, locate and re-establish a “voice” or essential agency for the neglected citizens in postcolonial India. Efforts to ameliorate their condition from the outside, she argued, would
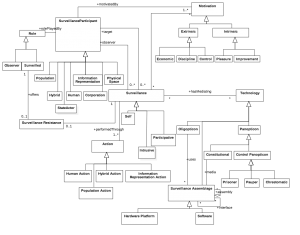
Towards a unified conceptual model for surveillance theories
Towards a unified conceptual model for surveillance theories

With my co-author, Prof Ravinder Barn, I have recently had a paper accepted at the ICSE Software Engineering in Society Track on a conceptual model for surveillance theories. The paper reviews the gamut of notions of surveillance from government to corporate surveillance to present a unified conceptual model.
Abstract
The erosion of values such as privacy can be a critical factor in preventing the acceptance of new innovative technology especially in challenging environments such as the criminal justice system. Erosion of privacy happens through either deliberate or inadvertent surveillance. Since Bentham’s original liberal project in the 1900s, a literature and a whole study area around theories of surveillance has developed. Increasingly this general body of work has focussed on the role of information technology as a vehicle for surveillance activity. Despite an abundance of knowledge, a unified view of key surveillance concepts that is useful to designers of information systems in preventing or reducing unintended surveillance remains elusive. This paper contributes a conceptual model that synthesises the gamut of surveillance theories as a first step to a theory building effort for use by Information Systems professionals. The model is evaluated using a design science research paradigm using data from both examples of surveillance and a recently completed research project that developed technology for the UK youth justice system.
The full paper will be available soon at the Middlesex University Repository link here. Meanwhile here is a taster of the conceptual model described in the paper.