The British Council has funded a number of projects aimed at developing research capacity in Vietnamese Universities. Middlesex University is working with several Universities from Vietnam as part of this set of projects. Our lead Vietnam partner is Van Lang University. The project is of course supported by the Faculty of Science and Technology at
Pirating the IBM 360 and PL/1 Pointers: Dinner at #ICSE2018
ICSE 2018 (https://www.icse2018.org), celebrating 50 years of software engineering, is promising to be great event. An outstanding set of keynote speakers including Fred Brooks Jr, Brian Randell and Margaret Hamilton (https://www.icse2018.org/info/keynotes) will bring to bear an insightful reflection on modern software engineering research and practice. Today, I had an opportunity to converse with two pioneers
The Link between Vienna, Fake Art, John Le Carre and Anthony Blunt
One of the great joys of travelling to different locations is to try and establish obscure links between things that you see on location and what you already know. So what connects the semantics of forged art with spies and Vienna? To establish the relationship you have to go Europe’s only art gallery devoted to
Using Foucault to examine value sensitive design concerns
One of the great benefits in multi-disciplinary ways of working is the exposure to other ways of examining problems. Last week, a paper submitted to CAISE 2018 (a top-ranked IS conference) was accepted for publication. The paper: Human and Value Sensitive Aspects of Mobile App Design: A Foucauldian Perspective examines the use of Michael Foucault’s writing on
Towards Improved Organisational Decision-Making – A Method and Tool-chain
It’s taken a bit of time, but one of our early experiments on constructing a tool chain from existing technology to support organisational decision making finally got accepted in the German Informatics Society journal: Enterprise Modelling and Information Systems Architectures Abstract Modern enterprises are large complex systems operating in an increasingly dynamic environment and are tasked
Are we all ‘Digital subalterns’ now?
In 1988, the postcolonial theorist, Gayatri Spivak published an essay “Can the Subaltern Speak?” about the appropriation of Gramsci’s “subaltern” (the economically dispossesed) term. She was critical of the effort to collect, locate and re-establish a “voice” or essential agency for the neglected citizens in postcolonial India. Efforts to ameliorate their condition from the outside, she argued, would
Examining the Interaction Between Fourth Estate and Twitter: An Exploratory Case Study
With my colleague Prof Franco Raimondi at Middlesex and colleagues Prof Ravinder Barn and Utsa Mukkerjee from social sciences at Royal Holloway, we did some twitter / machine learning based analysis on the broadcast of a BBC documentary called India’s Daughter. The broadcast caused ructions in the twitter community exposing some tensions around post colonialism
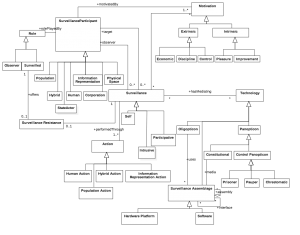
Towards a unified conceptual model for surveillance theories
Towards a unified conceptual model for surveillance theories

With my co-author, Prof Ravinder Barn, I have recently had a paper accepted at the ICSE Software Engineering in Society Track on a conceptual model for surveillance theories. The paper reviews the gamut of notions of surveillance from government to corporate surveillance to present a unified conceptual model.
Abstract
The erosion of values such as privacy can be a critical factor in preventing the acceptance of new innovative technology especially in challenging environments such as the criminal justice system. Erosion of privacy happens through either deliberate or inadvertent surveillance. Since Bentham’s original liberal project in the 1900s, a literature and a whole study area around theories of surveillance has developed. Increasingly this general body of work has focussed on the role of information technology as a vehicle for surveillance activity. Despite an abundance of knowledge, a unified view of key surveillance concepts that is useful to designers of information systems in preventing or reducing unintended surveillance remains elusive. This paper contributes a conceptual model that synthesises the gamut of surveillance theories as a first step to a theory building effort for use by Information Systems professionals. The model is evaluated using a design science research paradigm using data from both examples of surveillance and a recently completed research project that developed technology for the UK youth justice system.
The full paper will be available soon at the Middlesex University Repository link here. Meanwhile here is a taster of the conceptual model described in the paper.